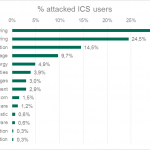
In the first half of the year manufacturing companies were most susceptible: ICS computers of them accounted for about one-third of all attacks, according to the Kaspersky Lab report “Threat Landscape for Industrial Automation Systems in H1 2017”. The peak of attackers’ activity was registered in March, after which the proportion of computers attacked gradually declined from April to June.
During the first six months of the year, Kaspersky Lab products blocked attack attempts on 37.6% of several tens of thousands of ICS computers protected of them globally. This figure was almost unchanged compared to the previous period – it is 1.6 percentage points less than in the second half of 2016.
Majority of them were in manufacturing companies that produce various materials, equipment and goods. Other most affected industries include engineering, education, food & beverage. ICS computers of energy companies accounted for almost 5% of all attacks.
While the top three countries with attacked industrial computers remained the same with Vietnam (71%), Algeria (67.1%) and Morocco (65.4%), researchers detected an increase in number of attacks in China (57.1%), which came fifth, according to the data released by Kaspersky Lab.
Also, experts discovered that the main source of threats was Internet: attempts to download malware or access known malicious or phishing web resources were blocked on 20.4% of ICS computers.
The reason of the high statistics for this type of infection lies in unrestricted access and connection of industrial networks to the Internet, which threatens the entire industrial infrastructure.
In total, in the first six months of 2017 Kaspersky Lab detected about 18,000 different modifications of malware on industrial automation systems belonging to more than 2,500 different families.
Ransomware Attacks
In the first half of the year the world has been facing the ransomware epidemic, which affected industrial enterprises as well. Based on the research of Kaspersky Lab ICS CERT, the number of unique ICS computers attacked by encryption Trojans had been increasing and tripled by June.
Overall, experts discovered encryption ransomware belonging to 33 different families. Most of the encryption Trojans have been distributed through spam emails, disguised as part of the business communication, with either malicious attachments or links to malware downloaders.
The main ransomware statistics from the H1, 2017 report include:
0.5% of computers in the industrial infrastructure of organizations were attacked by encryption ransomware at least once.
ICS computers in 63 countries across the globe were under numerous encryption ransomware attacks, the most notorious of which were WannaCry and ExPetr campaigns.
The WannaCry epidemic ranked highest among encryption ransomware families, with 13.4% of all computers in industrial infrastructure attacked. The most affected organizations included healthcare institutions and government sector.
The ExPetr was another most notorious encryption ransomware campaign of the first half of the year that attacked overall at least 50% of the companies from manufacturing, and Oil&Gas industries.
Top 10 most widespread encryption Trojan families include other ransomware families, such as Locky and Cerber, operating since 2016 and since that time earned the highest profit for cybercriminals.
“The fact that ICS computers in manufacturing companies accounted for about one third of all attacks, causes a great security concern, meaning high risks of cyberattack which could bring damages of enterprise’s industrial automation systems and serious consequences for businesses as a whole. Taking into consideration that in the first six months of the year we observed the active distribution of encryption malware, which we believe is set to continue, the probability of a destructive attack is even higher“, says Evgeny Goncharov, Head of Critical Infrastructure Defense Department, Kaspersky Lab.
In order to protect the ICS environment from possible cyber-attacks, Kaspersky Lab ICS CERT recommends the following:
Take an inventory of running network services with special emphasis on services that provide remote access to file system objects.
Audit ICS component access isolation, the network activity in the enterprise’s industrial network and at its boundaries, policies and practices related to using removable media and portable devices.
Verify the security of remote access to the industrial network, as minimum, and reduce or completely eliminate the use of remote administration tools as maximum.
Keep endpoint security solutions up-to-date.
Use advanced methods of protection: deploy tools that provide network traffic monitoring and detection of cyberattacks on industrial networks.